Blog

If your door is an ordinary one, there is only one way to unlock it – with a key. But what if you use Door Cloud for your doors? It turns out there are no fewer than 11 additional ways to open a door! Let’s take a look!
When it comes to access control, scalability is a cornerstone of ensuring security and operational efficiency, especially as organizations expand.

Key Link has proven to be a hugely practical solution for guest or visitor access. However, that alone is not yet a full, proper visitor management system.

What can we expect from AI? This question is currently is on the minds of almost everyone, including the access control community.

Did you know that Door Cloud offers a full-featured security management platform called "Incidents"?

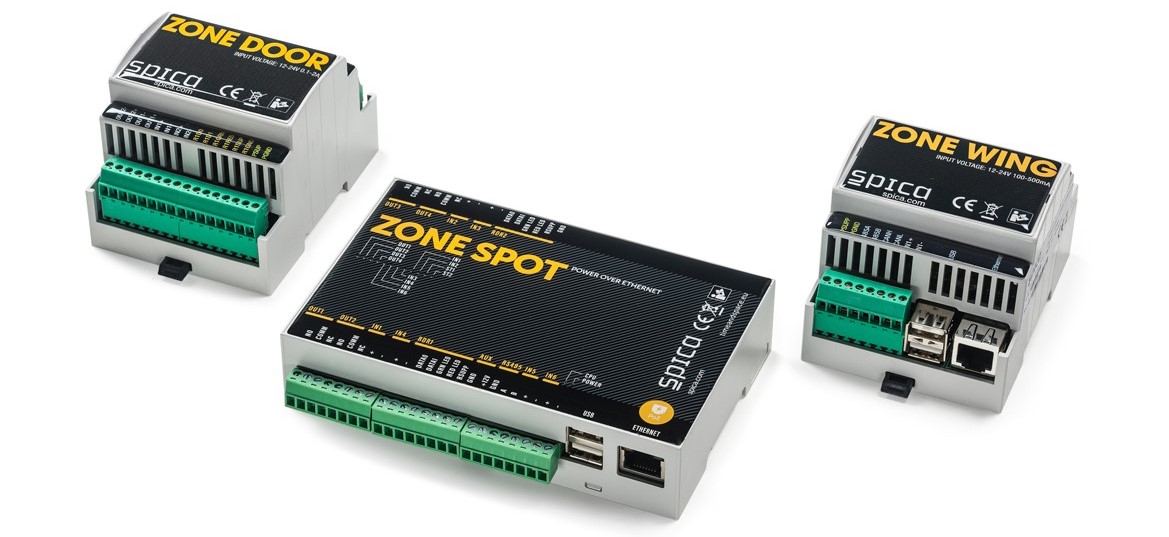
When we talk about wiring strategy in access control, we are really talking about controller networking. But before we get to that, what about wireless locks?

There are some really exciting times ahead for alarm management. Sensors are going wireless, the Internet of Things (IoT) is taking them directly to the cloud, and mobile is the “new normal” management platform.

These days the internet is quite reliable and dropouts are rare. The internet has become critical infrastructure, much like electricity.

Being the smartest access control in the cloud means that we can do some amazing things. One of such things is granting access via web link.

We are witnessing a huge IT migration to the cloud. General benefits of the cloud are well known, and they all apply to cloud access control.
There are many advantages of access control in the cloud. The main objection, however, has been internet security, or simply put the fear of hacking.

You have probably come across the new card reader connection standard called OSDP. OSDP stands for Open Supervised Device Protocol and is being endorsed by all major manufacturers.

Got another fancy loyalty card? It gives you a 20% discount for your next car rental, so you consider keeping it. But where?

There is a good chance that your company uses access control card readers. People who have the right security clearances can use their badges or cards on readers to enter rooms.

As we all know, one of the latest trends in Physical Access Control (PAC) is replacing cards with smartphones. This trend seems very natural.

Welcome to the Door Cloud blog! In our 1st post let’s ask ourselves the most fundamental question, why move to the cloud.
More good news, we have successfully passed the ISO/IEC 60839 level4 certification audit and now waiting for the formal paperwork. This is where we are at: https://t.co/JxKR9E5IwT. #ACaaS #criticalinfrastructure #resilience pic.twitter.com/9ccVv4ZXvJ
— Door Cloud (@Door_Cloud) April 4, 2025
How many ways to open a door should exist? How many do you need? https://t.co/RRrDNmQMlN #ACaaS #AccessControl
— Door Cloud (@Door_Cloud) August 19, 2024
Almost forgot to brag about this, back in June we successfully passed the ISO/IEC 27017 and 27018 certification audit and now waiting for the formal acknowledgement. Should we also get #SOC2, what do you think? #ACaaS pic.twitter.com/FKlVg3BK48
— Door Cloud (@Door_Cloud) July 24, 2024
Managing large access control system? See if you are missing something important at https://t.co/KLBSdBOsGb. #ACaaS #accesscontrol pic.twitter.com/CvpwecRBBM
— Door Cloud (@Door_Cloud) April 25, 2024
This ID card scanner from Dative is now supported as standard for #VisitorManagement. #ACaaS https://t.co/qH17PMc0yg pic.twitter.com/6IOYKBI5lI
— Door Cloud (@Door_Cloud) February 28, 2024

